#9 Nsec21 - Tom's Hut part2

If you want to fully understand this post I can only recommand you to read the previous one (Flag 8 part1)
RE102 Reverse
Like the previous one, the architecture is Xtensa, but this time I already have the right module for Ghidra !
Using Ghidra I’m doing the import and the analysis of the binary.
App Main
The app_main function is very similar to RE101, so this time let’s jump on the verify function !
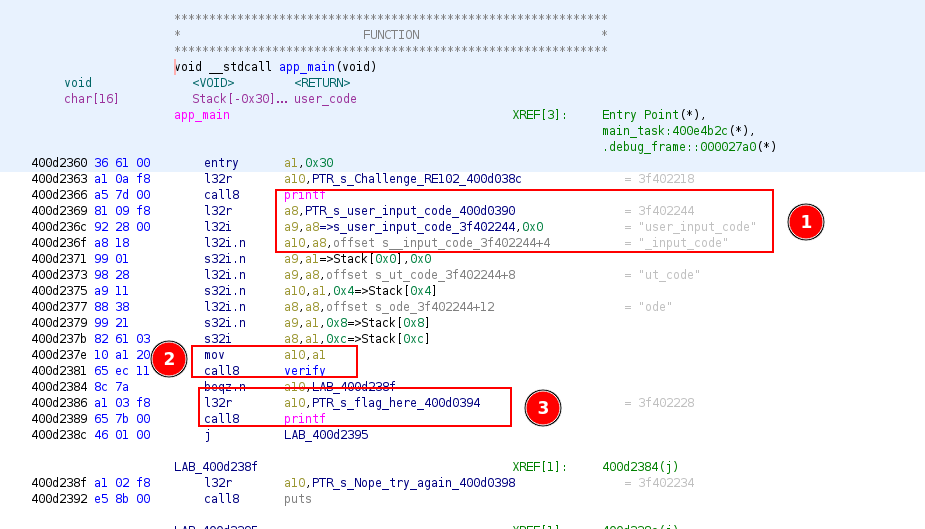
Verify
This time its different, as we can see the user input is stored inside user_code and the check is done using a8 registry.
In the first example, the first element of the input is checked with 0x66 which is a f.
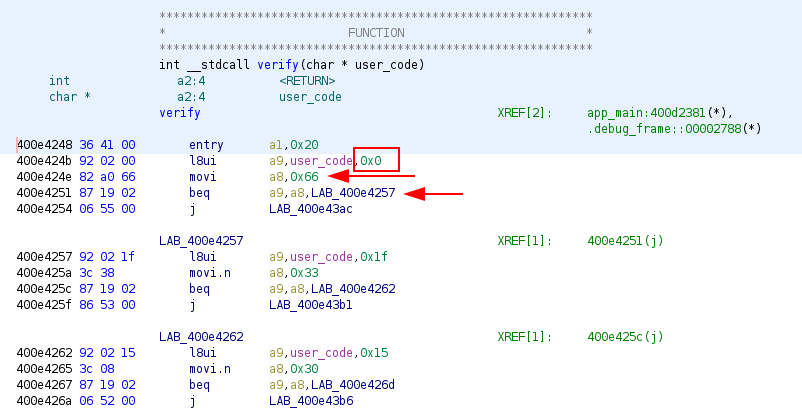
We just need to jump into each function and check which element is checked and with which character.
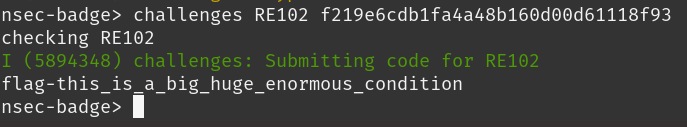
Flag
The final FLAG isf219e6cdb1fa4a48b160d00d61118f93